Keeping your data safe
Data Security
Reqi is built on top of the Azure Cloud, which is subject to numerous third-party security audits and follows the highest industry standards in information and operational security compliance certifications such as ISO 27001 and SOC-2. This means that Reqi is highly secure and reliable.
Our servers are located in an Australian data center, ensuring compliance with data protection schemes of this region. All data is encrypted at rest and in transit, and we use Azure Web Application Firewall to further enhance security. In summary, Reqi provides a secure and reliable online platform by utilizing the security features of Azure Cloud and by following the industry standards for data security and compliance.

Data Residency
Reqi uses Azure Cloud services to store client data, which adheres to a strict decommissioning policy to ensure data security and compliance. The data is deleted immediately when a client's services are decommissioned, and we also offer an option for automatic data purge on regular intervals if requested by the client.
Additionally, as part of contact tracing, each user's working data is stored, ensuring client's data is always safe. Reqi provides a secure and reliable online platform by utilizing the security features of Azure Cloud and by following strict data management protocols. It ensures that client's data is always safe and that data is deleted immediately when a client's service is decommissioned.

Reliability
Reqi is highly reliable, with a goal to achieve 99.9% uptime. We perform constant performance and load tests, and have 24/7 monitoring of services with alerts in case of any downtime. Additionally, Reqi employs various security measures to ensure data safety, such as security checks at every stage of the application pipeline, analysis of code for security loopholes before deployment, utilization of Software Composition Analysis (SCA) tools to prevent vulnerabilities in third-party libraries, and use of a Web Application Firewall (WAF) to prevent OWASP Top 10 vulnerabilities. All these measures make sure that Reqi is a secure and reliable online platform for managing requirements.

Data Security
To protect your data, we use a secure infrastructure, a dedication to dependability, and third-party testing.
Compliance
We are devoted to assisting you in meeting your compliance plans while also improving our own body of certifications.
Privacy
We take the security of your information extremely seriously. Our rules and processes are intended to keep this information safe.
Our Infastructure
Application Development
Authentication - Reqi employs strong security measures to ensure the protection of customer data. Authentication is done over encrypted connections and it supports integration with any Identity Provider that supports OIDC or SAML, including Google SSO and Microsoft. A strong password policy is in place to prevent easily guessable or brute-forceable passwords from being used.
Encryption - All data is encrypted at rest and in transit, and the minimum TLS version employed is 1.2 which ensures end-to-end security of data sent between applications over the Internet. Data at rest is encrypted with AES 256 to provide maximum protection for customer data. With these measures in place, Reqi provides a secure and reliable online platform for managing requirements and protecting customer data.

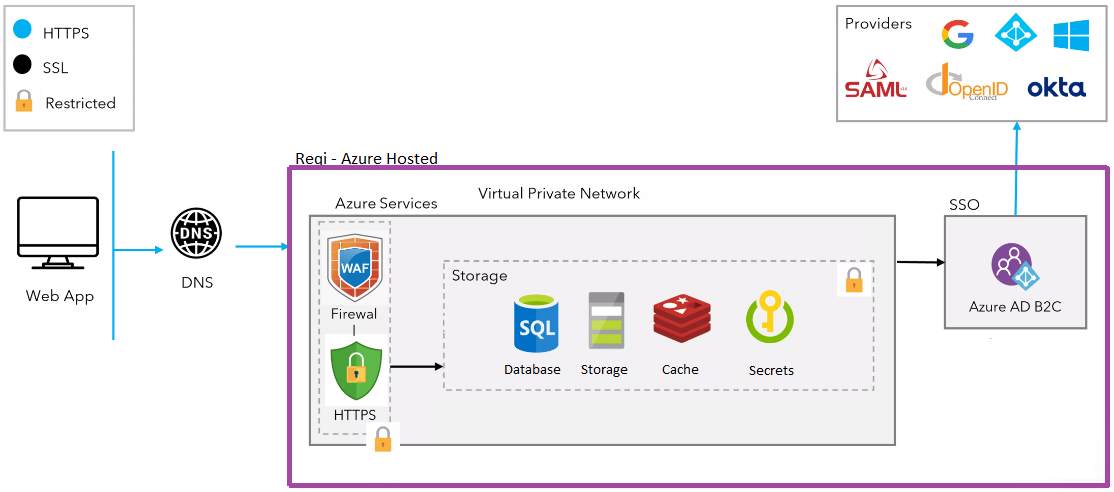
Data Collected
Reqi respects user's privacy and ensures that all the data collected is handled in a safe and secure manner. Our privacy policy includes an in-depth summary of the information we gather. For payments information, Reqi does not store credit/debit card information on our servers when a user signs up for a paid plan via credit/debit card. We use Stripe, which is a PCI-compliant service that securely stores sensitive payment data. This ensures that user's personal and financial information is kept secure. In summary, Reqi provides a secure and reliable online platform that respects user's privacy and securely handles all the data collected.

Disaster Recovery & Incident Response
Reqi has robust disaster recovery and incident response measures in place to ensure the continuity of its services. All assets are zone-redundant with automatic failover configured in case of an outage and the customer data Recovery-Time-Objective (RTO) is just 4 to 5 minutes. We have an extensive patch management procedure that ensures critical patches are applied within 48 hours of their release. In case of any outage to the services, it will be reported immediately and the first priority is identifying the compromised access, isolating or containing the damage, eradicating the offending component and putting measures in place to prevent the incident from recurring.
These measures demonstrate Reqi's commitment to providing a secure and reliable online platform that ensures continuity of services and protection of customer data.

Want to see more on how Reqi can help?
Reqi is a secure and reliable choice for requirements management. It utilizes industry-standard security protocols and technologies, such as encryption and firewalls, to protect client data. We maintain high uptime and have a strong incident response plan in place. Our support team is available to address any additional concerns.